Overview
Trezor.io/start serves as the official entry point for users who want to configure their Trezor hardware wallets safely and correctly. Hardware wallets remain one of the most secure storage options for cryptocurrencies because they operate offline, keeping private keys away from internet-based threats. As digital assets become increasingly valuable, the need for trustworthy self-custody solutions continues to rise. Trezor, one of the earliest hardware wallets introduced to the market, has earned a reputation for reliability, transparency, and strong cryptographic defenses. This guide outlines the essentials of the Trezor setup process, explains how the device protects your keys, and highlights best practices for maintaining long-term security.
By understanding each step of the onboarding flow, users minimize the risk of mistakes and build confidence in managing their own funds. Unlike custodial platforms where a third party controls the keys, Trezor puts full ownership back in your hands. This autonomy is one of the core principles of cryptocurrency, and Trezor helps users achieve it safely.
How Trezor Protects Your Private Keys
At the center of every Trezor device is a dedicated secure microcontroller designed to store sensitive cryptographic material. Private keys never leave this protected environment, even when the wallet is connected to a computer. Signing transactions happens internally within the device, and the user must physically approve each action on the screen. This process prevents remote tampering, as an attacker cannot sign a transaction without access to the physical hardware.
Trezor’s commitment to open-source firmware further strengthens its security posture. Anyone can review the code, audit it, and contribute improvements. Transparency reduces the likelihood of hidden weaknesses and encourages community oversight, which has helped maintain Trezor’s trusted status within the crypto ecosystem.
Preparing the Device for Safe Setup
Before beginning the configuration process, it is important to inspect the packaging. A legitimate Trezor device arrives sealed, and any sign of tampering should be treated as a warning. If the box appears opened or altered, do not continue with the setup—contact the retailer or manufacturer immediately. A secure supply chain is essential because the trust model assumes the device is safe from the moment it is unboxed.
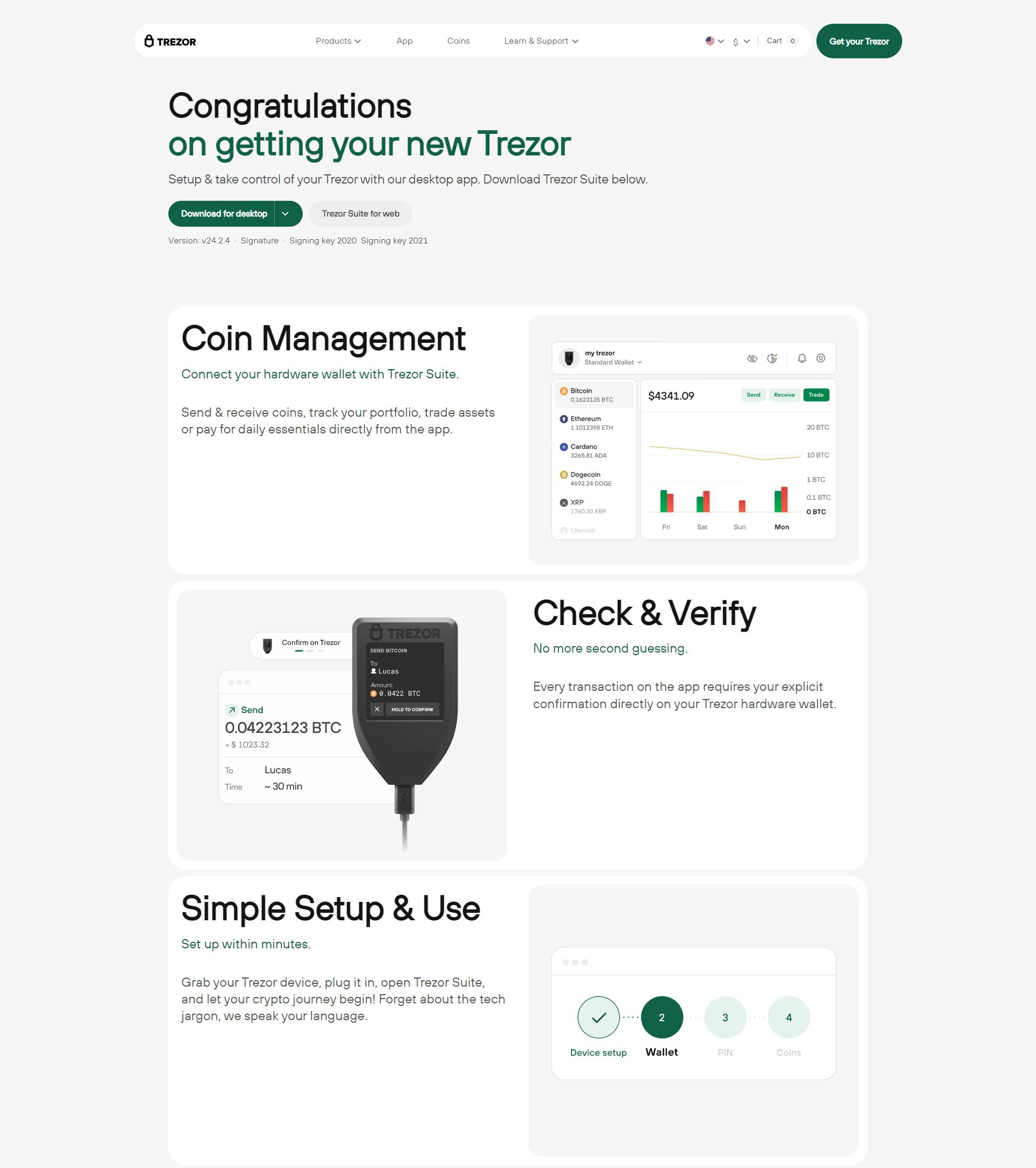
Once authenticity is confirmed, users should visit the official onboarding portal and download Trezor Suite. This application guides the initialization process, helps manage accounts, installs firmware updates, and connects you safely to the blockchain. The interface is designed to be intuitive while still offering advanced features for experienced users.
Setting Up Your Wallet
During initialization, the device will prompt you to create a PIN code. This PIN prevents unauthorized access if the wallet is lost and protects the device from being used without permission. After the PIN is set, Trezor generates a recovery seed consisting of 12 or 24 words. This seed is the master backup and must be recorded carefully because it is the only way to restore your wallet if the device becomes damaged or misplaced.
The recovery seed should always be stored offline. Many users choose metal backup plates because they resist fire, water, and physical degradation far better than paper. Digital storage—such as taking photos or saving the seed in cloud applications—creates unnecessary risk and should be avoided entirely.
Managing Assets Through Trezor Suite
After initialization, Trezor Suite serves as your control panel. You can add accounts, monitor balances, send transactions, and view detailed activity logs. The software supports numerous cryptocurrencies and continues to expand its asset list as the market evolves. Despite this flexibility, the security model remains consistent: every transaction must be confirmed on the physical device.
For advanced users, Trezor Suite offers passphrase support, portfolio views, and integration with third-party services. Beginners benefit from a clean interface that simplifies complex processes. Regardless of experience level, private keys remain stored securely inside the hardware, never exposed to external applications.
Maintaining Strong Security Habits
Owning a secure hardware wallet does not eliminate the need for responsible behavior. Users must never share their recovery seed, never enter it into websites, and always remain cautious of phishing attempts. Fake websites often mimic official portals, so verifying the URL is essential before downloading anything. Firmware updates should also be installed promptly because they patch vulnerabilities and improve overall device robustness.
Conclusion
Trezor hardware wallets offer a dependable and transparent solution for anyone seeking secure self-custody of their cryptocurrencies. By keeping private keys offline, requiring physical transaction approval, and embracing open-source principles, Trezor provides a high level of assurance in an increasingly hostile digital environment. Proper setup, careful storage of the recovery seed, and consistent security practices ensure that your funds remain protected over time. As digital assets continue to grow in significance, trusted hardware wallets like Trezor remain essential tools for safeguarding financial independence.